The digital world is full of escalating cybersecurity threats, and staying
ahead requires more than traditional defenses—it demands adaptive, AI-powered solutions .
At Acclyne, our Cybersecurity & Compliance serves as a bulwark of protection against these challenges.
We build a fortress rooted in vigilance, adaptability, and steadfast security, ensuring a secure ecosystem
where threats are thwarted and vulnerabilities are sealed before they can be exploited.
Our cybersecurity experts and AI specialists collaborate seamlessly to fortify your
digital assets while maintaining strict adherence to regulatory compliance. From proactive
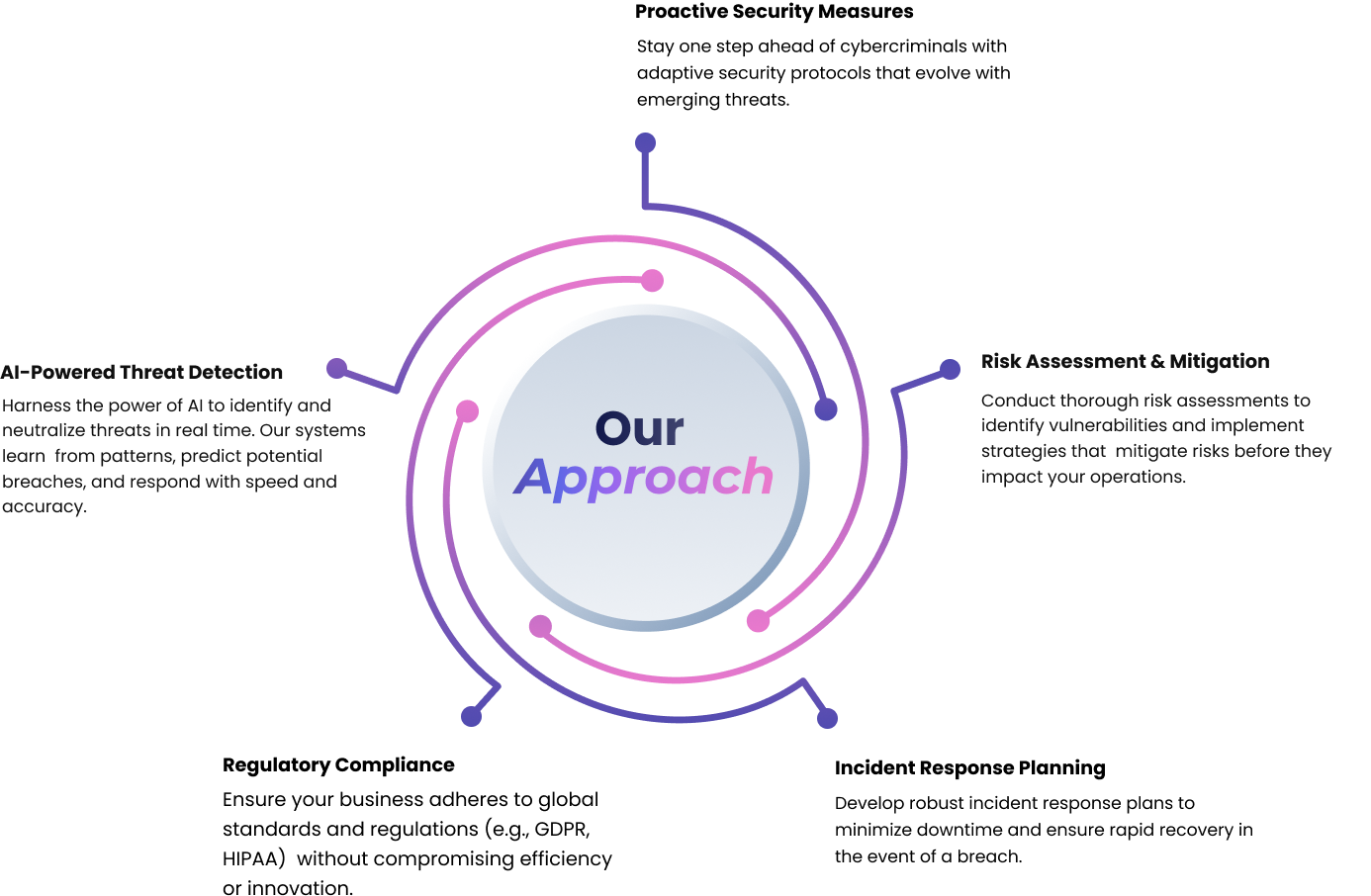
threat detection to comprehensive risk assessment, we optimize security measures and navigate the
ever-changing compliance landscape with precision. By leveraging AI-driven insights, we create a blueprint
for your business’s secure and thriving digital future .
with AI-Driven Security
At Acclyne, we leverage advanced AI-driven techniques to help you quantify and communicate security risks by striking the perfect balance between reliability and protection. Our team takes the lead in creating and maintaining comprehensive security documentation tailored to your unique needs. From threat modeling to privacy protection, we ensure compliance and security requirements are seamlessly integrated into your project’s planning and architecture—providing robust protection from the very beginning.
Threat Modeling

Identify, assess, and mitigate potential threats before they impact your systems. Our AI-powered tools simulate attack scenarios, enabling proactive risk management and ensuring your defenses are always one step ahead.
Secure Network Design

Architect resilient, secure networks that safeguard your data and operations. By integrating AI-driven insights, we design network infrastructures that adapt to emerging threats while maintaining optimal performance.
Application Security Review

Conduct thorough assessments of your applications to identify vulnerabilities and ensure compliance with industry standards. Our reviews go beyond surface-level checks, providing actionable recommendations to fortify your software.
Compliance Assessment

Ensure your systems meet global regulatory standards (e.g., GDPR, HIPAA) without compromising efficiency or innovation. Our AI-driven audits streamline compliance processes, reducing risks and enhancing trust.
Security Audits

Perform rigorous, end-to-end audits to evaluate your security posture. Our AI-enhanced tools detect anomalies, predict risks, and provide actionable insights to strengthen your defenses.
Privacy Protection

Safeguard sensitive data with cutting-edge privacy solutions. From encryption to anonymization, we ensure your data remains secure while adhering to privacy regulations and best practices.
As businesses increasingly migrate to the cloud, the need for robust cloud security solutions becomes paramount. Acclyne offers comprehensive cloud security services designed to protect your data, applications, and infrastructure across various cloud platforms. We implement AI-driven security measures that ensure continuous monitoring, threat detection, and compliance within your cloud ecosystem. Our approach focuses on securing your cloud journey from initial migration to ongoing operations.
Cloud Security Architecture

Design and implement secure cloud environments, incorporating best practices and AI-driven security controls to protect your assets.
Cloud Data Protection

Implement robust encryption, access controls, and data loss prevention strategies to safeguard sensitive information stored in the cloud.
Identity and Access Management (IAM) for Cloud

Configure and manage IAM policies to ensure least privilege access and prevent unauthorized entry to cloud resources.
Cloud Security Posture Management

Continuously monitor your cloud configurations for misconfigurations and security risks, leveraging AI for proactive identification and remediation.
Container Security

Secure your containerized applications (e.g., Docker, Kubernetes) throughout their lifecycle, from development to deployment and runtime.
In an era of stringent data protection regulations, ensuring robust data privacy and governance is not just a compliance requirement but a cornerstone of trust. Acclyne helps organizations establish comprehensive data privacy frameworks, ensuring adherence to global regulations and best practices. We implement solutions that manage the entire data lifecycle, from collection and storage to processing and deletion, with a focus on privacy by design.
Data Mapping and Inventory

Create a comprehensive understanding of your data assets, where they reside, and how they are processed.
Privacy Impact Assessments

Conduct assessments to identify and mitigate privacy risks associated with new projects, systems, or data processing activities.
Data Minimization & Anonymization

Implement strategies to reduce the amount of personal data collected and to anonymize or pseudonymize data where appropriate.
Consent Management

Develop and implement mechanisms for managing user consent for data collection and processing, ensuring transparency and control.
Data Breach Notification Planning

Establish clear procedures and communication plans for responding to and notifying relevant parties in the event of a data breach.
A modern Security Operations Center (SOC) is critical for real-time threat detection and rapid incident response. Acclyne provides advanced SOC services, offering 24/7 monitoring, analysis, and response to security incidents. SOC can leverage AI and machine learning to sift through vast amounts of data, identify anomalies, and provide actionable intelligence, allowing for swift and effective threat neutralization.
Security Monitoring and Alerting

Continuous monitoring of your IT infrastructure, networks, and applications for suspicious activities and potential threats.
Threat Intelligence Integration

Incorporate up-to-date threat intelligence feeds to enhance detection capabilities and anticipate emerging attack vectors.
Incident Detection and Analysis

Rapidly detect and analyze security incidents, determining their scope, impact, and root cause.
Security Incident Response

Orchestrate and execute swift incident response plans to contain breaches, eradicate threats, and restore operations.
Vulnerability Management

Proactive identification and prioritization of vulnerabilities within your systems, with recommended remediation strategies.
With Acclyne’s Cybersecurity & Compliance expertise, you can protect
your digital assets and thrive in an increasingly complex threat
landscape.